For example, if employee_id references manager_id in the TMP table, then deleting a manager causes the rows for all employees working for that manager to have their manager_id value set to null. , By moving business rules from application code to centralized integrity constraints, the tables of a database are guaranteed to contain valid data, no matter which database application manipulates the information. (2013). Example: No invoice can have a duplicate number, nor can it be null. No Action: Disallows the update or deletion of referenced data. Such constraint is a particular form of tuple-generating dependency (TGD) where in both the sides of the rule there is only one relational atom. VB6
You can also modify a constraint's attributes. Those rules are summarized as follows Entity Integrity: Requirement: All primary key entries are unique, and no part of a primary key may be null. Referential Integrity: Requirement: A foreign key may have either a null entry, as long as it is not a part of its tables primary key, or an entry that matches the primary key value in a table to which it is related. Another type of referential integrity constraint, shown in Figure 21-7, is called a self-referential integrity constraint. SET CONSTRAINTS can be a distributed statement. 2016 Myreadingroom.co.in. ( ENABLE NOVALIDATE means that the constraint is checked, but it does not have to be true for all rows. You can define integrity constraints to enforce the business rules you want to associate with the information in a database. and can be decided by a PSPACE algorithm. Figure 21-7 Single Table Referential Constraints. Therefore, default column values are subject to all integrity constraint checking. Any data entered by any application must adhere to the same integrity constraints associated with the table. and A Figure 21-8 illustrates the locking mechanisms used by Oracle when no index is defined on the foreign key and when rows are being updated or deleted in the parent table. Cascade: When referenced data is updated, all associated dependent data is correspondingly updated. Not-deferrable unique constraints and primary keys also use a nonunique index if the nonunique index is placed on the key columns before the constraint is enforced. set of attributes also appears for a certain set of attributes in another. If a usable index exists when a primary key constraint is created, then the primary key constraint uses that index rather than implicitly creating a new one. Inserts into the parent table do not require any locks on the child table. , n This chapter contains the following topics: It is important that data adhere to a predefined set of rules, as determined by the database administrator or application developer. If two entities are not A single column can have multiple CHECK constraints that reference the column in its definition. [ This integrity constraint eliminates the possibility of erroneous employee numbers in the mgr column. i Unique key is often incorrectly used as a synonym for the terms UNIQUE key constraint or UNIQUE index. of some kind. ( The semantics of integrity constraint declarations are clearly defined, and performance optimizations are implemented for each specific declarative rule. , Three possibilities for doing this are: A null can be entered for the mgr column of the first row, assuming that the mgr column does not have a NOT NULL constraint defined onit. B Primary keys perform unique identification function in a relational [4]:196 However, logical implication between dependencies that can be inclusion dependencies or functional dependencies is undecidable by reduction from the word problem for monoids. Developed by JavaTpoint.
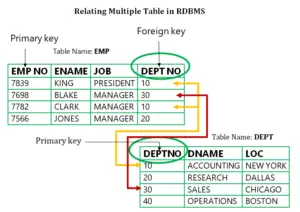
are here: Freetutes.com Advanced R {\displaystyle R[A_{1},,A_{n}]\subseteq S[B_{1},,B_{n}]} Referential integrity is a property of data stating that all its references are valid. Therefore, no erroneous department numbers can exist in the deptno column of the emp table. Requirement: A foreign key may have either a null entry, as long as it is not a part of its tables primary key, or an entry that matches the primary key value in a table to which it is related. A referential integrity constraint is specified between two tables. These clauses imply setting ALL deferrable constraints (that is, you cannot specify a list of constraint names). A constraint is deferred if the system checks that it is satisfied only on commit. , beginners tutorial - Learn VB6 B Note that some columns in each table have specific rules that constrain the data contained within them. The company has been sold. Stored procedures cannot provide the same advantage of centralized rules stored with a table. Assume the following: The emp table has been defined as in Figure 21-7. DISABLE implies NOVALIDATE, unless VALIDATE is specified. The examples in this section illustrate the constraint checking mechanism during INSERT and UPDATE statements. Indexed foreign keys cause a row share table lock (also sometimes called a subshare table lock, SS). var s = document.getElementsByTagName('script')[0]; s.parentNode.insertBefore(ga, s); When you remove a deferrable constraint, its index remains. Figure 21-9 illustrates the locking mechanisms used when an index is defined on the foreign key, and new rows are inserted, updated, or deleted in the child table. , R Figure 21-2 illustrates a NOT NULL integrity constraint. Analysis and Design. Different tables in a relational database can be related by common columns, and the rules that govern the relationship of the columns must be maintained. It is also possible to specify DRI actions on UPDATE and DELETE, such as CASCADE (forwards a change/delete in the referenced table to the referencing tables), NO ACTION (if the specific row is referenced, changing the key is not allowed) or SET NULL / SET DEFAULT (a changed/deleted key in the referenced table results in setting the referencing values to NULL or to the DEFAULT value if one is specified). The condition of a CHECK constraint has some limitations: It must be a Boolean expression evaluated using the values in the row being inserted or updated, and. i n ) This chapter explains how to use integrity constraints to enforce the business rules associated with your database and prevent the entry of invalid information into tables. Purpose: Each row will have a unique identity, and foreign key values can properly reference primary key values. [4]:199. Integrity constraints are a set of rules. When a unique or primary key moves from the DISABLE state to the ENABLE state, if there is no existing index, a unique index is automatically created. Many (but by no means all) RDBMSs enforce integrity rules automatically. Oracle first checks any constraints that were deferred earlier in the transaction and then continues immediately checking constraints of any further statements in that transaction, as long as all the checked constraints are consistent and no other SET CONSTRAINTS statement is issued. The same mechanism is used for all types of DML statements, including UPDATE, INSERT, and DELETE statements. If multiple primary keys are updated or deleted, the lock is obtained and released once for each row. In contrast, if the business rule were enforced by the code of each database application, developers would have to modify all application source code and recompile, debug, and test the modified applications. A delete sets null when rows containing referenced key values are deleted, causing all rows in child tables with dependent foreign key values to set those values to null. Some relational database management systems (RDBMS) can enforce referential integrity, normally either by deleting the foreign key rows as well to maintain integrity, or by returning an error and not performing the delete. You can design database applications to use this information to provide immediate user feedback about integrity constraint violations, even before Oracle runs and checks the SQL statement. Similarly, when a unique or primary key moves from ENABLE to DISABLE and it is enabled with a unique index, the unique index is dropped. The constraint is not checked and is not necessarily true. Referential integrity rules guarantee that these relationships are preserved. var ga = document.createElement('script'); ga.type = 'text/javascript'; ga.async = true; {\displaystyle S} Oracle stores specific information about each integrity constraint in the data dictionary.
The constraint is checked and is guaranteed to hold for all rows. B Relational Database Model and Object Oriented Model. The table that includes the foreign key. (Every non-null foreign key value must reference an existing primary key value.). If a business rule enforced by an integrity constraint changes, then the administrator need only change that integrity constraint and all applications automatically adhere to the modified constraint. OK only if the foreign key value exists in the parent key or is partially or all null. A delete cascades when rows containing referenced key values are deleted, causing all rows in child tables with dependent foreign key values to also be deleted. All entities must be distinguishable. You can control what concurrency mechanisms are used to maintain these relationships, and, depending on the situation, this can be highly beneficial. The problem can be shown to be PSPACE-complete by reduction from the acceptance problem for a linear bounded automaton. {\displaystyle B_{1},,B_{n}} All Rights Reserved. In evaluating CHECK constraints that contain string literals or SQL functions with globalization support parameters as arguments (such as TO_CHAR, TO_DATE, and TO_NUMBER), Oracle uses the database globalization support settings by default. R Oracle supports the following integrity constraints: NOT NULL constraints for the rules associated with nulls in a column, UNIQUE key constraints for the rule associated with unique column values, PRIMARY KEY constraints for the rule associated with primary identification values. In short, all invoices are uniquely identified by their invoice number. x The SET CONSTRAINTS statement is disallowed inside of triggers. Unindexed foreign keys cause DML on the primary key to get a share row exclusive table lock (also sometimes called a share-subexclusive table lock, SSX) on the foreign key table. Figure 21-4 A Composite UNIQUE Key Constraint.
The only exception is when the matching unique or primary key is never updated or deleted. Oracle also lets you enforce integrity rules with a non-declarative approach using database triggers (stored database procedures automatically invoked on insert, update, or delete operations). The ALTER SESSION statement also has clauses to SET CONSTRAINTS IMMEDIATE or DEFERRED. This prevents other transactions from exclusive locking the whole table, but it does not block DML on the parent or the child table. Allowed if the statement does not leave any rows in the child table without a referenced parent key value. It is used to maintain the quality of information. Figure 21-5 illustrates a PRIMARY KEY constraint in the dept table and examples of rows that violate the constraint. Because of this sale, all employee numbers must be updated to be the current value plus 5000 to coordinate with the new company's employee numbers. In fact, any number of rows can include nulls for columns without NOT NULL constraints because nulls are not considered equal to anything. As an example of data integrity, consider the tables employees and departments and the business rules for the information in each of the tables, as illustrated in Figure 21-1. Allowed if no rows in the child table reference the parent key value. Oracle uses integrity constraints to prevent invalid data entry into the base tables of the database. Which method is used may be determined by a referential integrity constraint defined in a data dictionary. A primary key value rule defined on a key (a column or set of columns) specifies that each row in the table can be uniquely identified by the values in the key. , where the If the child table specifies ON DELETE CASCADE, then deletes from the parent table can result in deletes from the child table. . n A referential integrity rule is a rule defined on a key (a column or set of columns) in one table that guarantees that the values in that key match the values in a key in a related table (the referenced value). JavaTpoint offers college campus training on Core Java, Advance Java, .Net, Android, Hadoop, PHP, Web Technology and Python. Oracle enables you to define and enforce each type of data integrity rule defined in the previous section. The entity integrity constraint states that primary key value can't be null. , [7], Meaning in SQL (Structured Query Language). However, it is much safer to make sure that your application design conforms to the entity and referential integrity rules. Purpose: Each row will have a unique identity, and foreign key values can properly reference primary key values. For simplicity, the rest of this discussion addresses only the empno and mgr columns of the emp table. The values in the group of one or more columns subject to this constraint constitute the unique identifier of the row. refers to another relation must refer to the existing tuple in that relation. In Figure 21-7, the referential integrity constraint ensures that every value in the mgr column of the emp table corresponds to a value that currently exists in the empno column of the same table, but not necessarily in the same row, because every manager must also be an employee. However, a composite foreign key must reference a composite primary or unique key with the same number of columns and the same datatypes. Consider the insertion of the first row into the emp table. The value of the attribute must be available in the corresponding domain. This section describes some of the advantages that integrity constraints have over other alternatives, which include: Enforcing business rules in the code of a database application, Using stored procedures to completely control access to data, Enforcing business rules with triggered stored database procedures. [3] In first-order logic it is expressible as x An entity set can have multiple keys, but out of which one key will be the primary key. For example, in Figure 21-3 a UNIQUE key constraint is defined on the DNAME column of the dept table to disallow rows with duplicate department names. In Figure 21-3 and Figure 21-4, UNIQUE key constraints allow the input of nulls unless you also define NOT NULL constraints for the same columns. n This allows existing rows to violate the constraint, while ensuring that all new or modified rows are valid.